Fill the Form below or simply send a mail to engrifeanyi@gmail.com

Hello, Kedu, नमस्ते!
I protect you and your organisation from Cyber Threats, Vulneabilities and Attacks while effectively managing your IT and Cloud infrastructures.
About me
Ifeanyi Barth is a dedicated professional with a B.Eng in Electrical and Electronics Engineering, an (ISC)² Certified Cybersecurity Professional, and a passionate innovator in IoT technology. As the founder and Technical Director of CyberBill Africa, I empower individuals of all ages—children, teenagers, students, and adults—through comprehensive training in IT, programming, cybersecurity, and IoT applications. My work bridges the digital divide by equipping learners with skills to thrive in a connected world, from coding secure apps to designing smart systems like solar IoT solutions.
With years of industry experience, I offer consultancy services in information security (Infosec), cyber safety, and IoT system resilience. At Net & Jud Resources, I deployed cloud-connected solar IoT systems using MQTT and AWS, securing them against threats like breaches and DDoS attacks. My goal is to help individuals and organizations protect their digital and physical assets—whether it’s sensitive data or IoT-driven infrastructure—through vulnerability analysis, risk mitigation, and tailored security frameworks.
As a cloud and IoT engineer, I specialize in integrating scalable, efficient technologies. From transitioning businesses to cloud platforms (AWS, Azure) to optimizing IoT ecosystems for energy management, I guide clients through design, implementation, and management. My expertise ensures robust, low-power solutions that harness the full potential of cloud and IoT, minimizing complexity while maximizing impact.
Rooted in a deep understanding of client needs, my approach blends clear communication, meticulous detail, and continuous learning in the fast-evolving tech landscape. Whether enhancing cybersecurity, developing programming skills, securing IoT deployments, or leveraging cloud solutions, I deliver personalized, high-impact results. Let’s connect to explore how my expertise can empower you in the digital and IoT realm—reach out today!
Core Competence

Services
Training and Certification
The Digital Sprinters report highlights the potential for accelerated economic growth in Africa through digital transformation, emphasizing the importance of skills development for its citizens. The demand for cybersecurity skills is on the rise globally, with an estimated 3.5 million cybersecurity job vacancies currently available, compared to just 1 million in 2013. In Africa, preventing cybercrime through cybersecurity measures could save up to $4 billion annually. However, there is a shortage of trained cybersecurity professionals, as a recent survey revealed that two-thirds of enterprises face challenges in recruiting and retaining qualified experts in this field. Check out our various programmes designed to help you
Professional IoT Solutions
CyberBill provides expert IoT services to meet the growing demand for connected technologies. We design, deploy, and manage efficient IoT systems, including cloud-connected solar solutions using MQTT and AWS. Our tailored, secure, and scalable deployments—spanning cloud platforms like AWS and Azure—optimize performance and protect your assets.
IT Support & Security
Cybercrime is on the increase in our world and the need to protect one's self and organization has never been more important than now. A report released by FBI indicates that in 2021 alone they got a report of over 850,000 of cybercrimes and a lost of almost $7 billion. This is only in the United States. Global cybercrime damages are predicted to cost up to $10.5 trillion annually by 2025 according to a report by Cybersecurity Ventures. I am trained to employ various tools and techniques to help your organisation stay safe in this era.
Cloud Computing and Security
Many smart businesses are moving their operations to the cloud. Cloud computing with its intending benefits is now the order of the day in running organisation's infrastructure. I help your organisation migrate to popular Cloud Service Providers like Amazon Web Services, Microsoft Azure, Google Cloud etc. I can also help in managing the resources and training the workforce in effective use of cloud computing while ensuring security of data hosted on the cloud.
Programming, Scripting and Process Automation
Daily running of business requires lots of processes and this could be cumbersome sometimes as one have to repeat numerous processes everyday. Luckily the repeated processes are often time the same; this offers us the opportunity to automate this processes using various computer programming techniques. I use python and bash shell programming and scripting to help your organisation solve this critical problem while making your staff work effectively and efficiently.
E-Government
I help your government to develop models to implement an Electronic Government. A government run effectively with technology. A society where government services can be accessed through web and mobile applications using PCs and smartphones.
Blockchain Security
Blockchain security is a complete risk management system for blockchain networks, incorporating assurance services, cybersecurity frameworks, and best practices to mitigate the risks of fraud and cyber-attacks. I employ cybersecurity frameworks, security testing methodologies, and secure coding practices to protect your Blockchain solution from online frauds, breaches, and other cyberattacks.
18
Certifications
20
Satisfied Clients
23
Projects
35
Reports and Blog Posts
My Works
I have worked on dozens of projects so I have picked only the latest for you.
- All
- Amazon Web Service
- Microsoft Azure Service
- Linux
- Python
- Information Security
- Developing Projects

This Repo contains a python scripts that accepts input from user and perform basic mathematical operations like Addition Subtraction Division Multiplication. It does this by allowing the user to select their desired mathematical operation While returning "invalid" when other operations are entered. We are currently still working to include other mathematical operations in the script
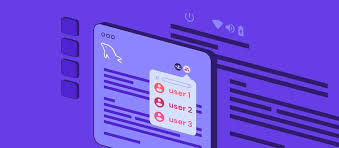
This Repo shows us the steps involve in data protection especially Social Media Accounts. Multi-factor Authentication (MFA) is an authentication method that requires the user to provide two or more verification factors to gain access to a resource such as an application, online account, or a VPN. MFA is a core component of a strong identity and access management (IAM) policy. Rather than just asking for a username and password, MFA requires one or more additional verification factors, which decreases the likelihood of a successful cyber attack.

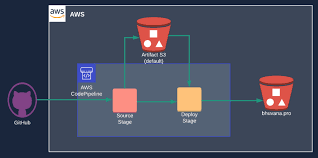
This Repo shows us the steps involve in creating an Amazon Load Balancer. Elastic Load Balancing automatically distributes your incoming traffic across multiple targets, such as EC2 instances, containers, and IP addresses, in one or more Availability Zones. It monitors the health of its registered targets, and routes traffic only to the healthy targets.

This Repo shows Python Script for Diaspora Voting Verification Sysyem. The prospective voter is required to enter their full name as it appears on their passport. They are also required to enter their passport serial number.
The Program first matches the provided name and passport serial number to the data available in the system's database. If the provided data is correct then the program goes ahead to check the age of the passport carrier as it is contained in its details. If the age is up to 18 years, they are allowed to vote else they are denied such access.